I blogged last year about ownership, control, and possession in relation to high-value cryptographic keys, in particular those used with an organization’s applications in the cloud. The main considerations and themes still hold true: Organizations should first ensure that sensitive data is encrypted before transitioning to the cloud.
Choosing the right key management trust model is often informed by the level of ownership, control, and possession an organization wants to adopt, as well as the operational cost associated with each model:
- Ownership specifies to whom the cryptographic keys that encrypt and protect those workloads belong. In the common cloud security responsibility matrix, information and data is always the responsibility of the cloud consumer.
- Control specifies who can carry out the various key management lifecycle tasks. Having control means being able to carry out key lifecycle tasks and often automating them but also includes precluding others from this capability.
- Possession or holding specifies who owns the infrastructure or geographic location where the keys physically reside.
More regulated industries have their options prescribed by security and data handling policies, government mandates (data sovereignty considerations for example), and the overall security posture of the organization. Data sovereignty has recently become a hot potato in the European Union, where the outcome of the Schrems II legal case has led to over 5,000 organizations having to think carefully about where their cryptographic keys and encrypted data reside.
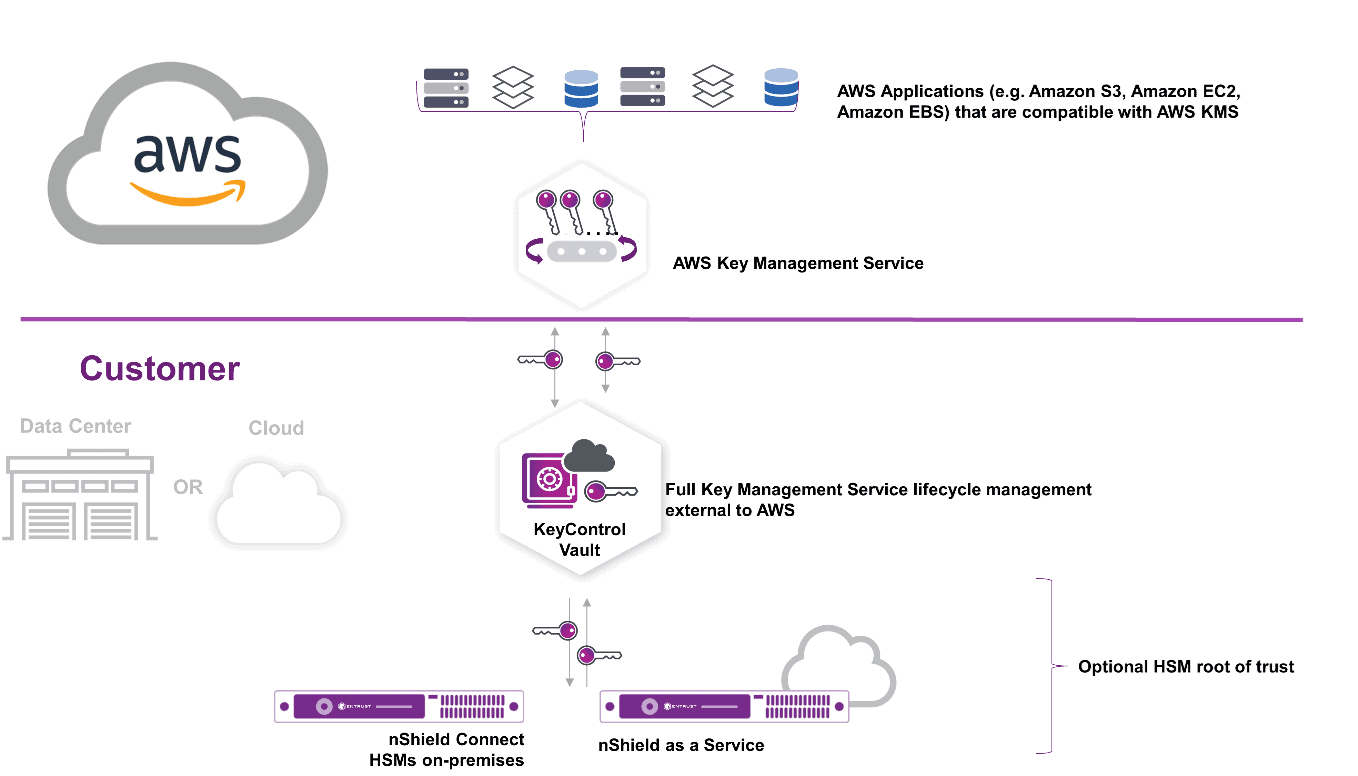
As a leading cloud infrastructure provider, AWS responded in November to customers seeking maximum ownership, control, and possession of their cryptographic keys by introducing the AWS Key Management Service (AWS KMS) External Key Store or AWS XKS. It empowers organizations to own, hold, and manage their cryptographic keys on premises or in a cloud-based solution under their control, completely outside of the AWS ecosystem. As AWS explains it:
“At a high level, AWS KMS forwards API calls to securely communicate with your HSM (or key management solution). Your key material never leaves your HSM (or key management solution). This …. allows you to encrypt data with external keys for the vast majority of AWS services that support AWS KMS customer managed keys, such as Amazon EBS, AWS Lambda, Amazon S3, Amazon DynamoDB, and over 100 more services.”
Entrust has been working with AWS to provide a seamless XKS integration with Entrust KeyControl software, leveraging its key vault architecture underpinned by an Entrust nShield hardware security module (HSM) as the root of trust. Entrust in conjunction with AWS can help organizations that have high-value workloads protected by cryptographic keys and face strong data sovereignty or regulatory mandates to choose the right level of ownership, control, and possession to meet their security needs.
So, if you are already using AWS services or are planning to migrate to the cloud in the near future and are concerned about the impact of the ownership, possession, and control of your keys, consider Entrust KeyControl for XKS.