My favourite scene from mid-80’s movie Ferris Bueller’s Day Off, was when Ferris (Matthew Broderick) and his friends roll into a rather shady looking valet car park in a ‘borrowed’ vintage Ferrari California Spyder. The dodgy looking valet car park attendant says “Uh… you fellas have nothing to worry about. I’m a professional” as he is handed the keys to the stunning car. Watching the film, you know exactly what’s coming next.
The valet parking scene got me thinking about a different type of high value key – cryptographic keys, in particular those used with an organization’s applications in the cloud. When migrating from on premises to the cloud, organizations have several deployment options available to them. Choosing their preferred option is often informed by the level of Ownership, Control and Possession (OCP) that they want to adopt:
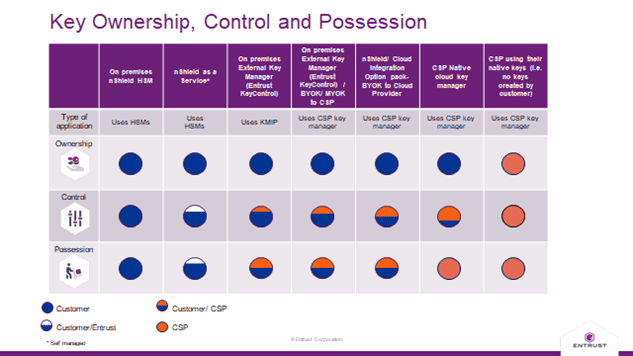
- Ownership specifies to whom the cryptographic keys that encrypt and protect those workloads belong. In the common cloud security responsibility matrix, information and data is always the responsibility of the cloud consumer.
- Control specifies who can carry out the various key management lifecycle tasks. Having control means being able to carry out key lifecycle tasks and often automating them but also includes precluding others from this capability.
- Possession or holding specifies who owns the infrastructure or geographic location where the keys physically reside.
When moving applications and data to the cloud, organizations need to think about how the level of Ownership, Control and Possession changes from the on-premises model. On premises, the Security Officer oversaw the creation and control of these keys, they had complete ownership, control, and possession. Migrating to the cloud, decisions may be informed by security and data handling policies, government mandates (data sovereignty considerations for example) and the overall security posture of the organisation.
As a first option, major public cloud providers typically offer their own native key management server (KMS). Security conscious organizations that want to own and control their keys throughout their lifecycle may have some reservations with this approach. The confidentiality and integrity of major cloud service providers are considered strong and well-attested, however, by their nature they can be opaque since you do not have visibility under the CSPs (Cloud Service Providers) hood. Here Ownership is retained by the organization – they own the keys. Control is shared, the organization can send commands via the CSP’s tools and automate the key usage but ultimately, it’s all in the CSP infrastructure. Possession is held by the CSP.
Another approach open to organizations is to opt for a dedicated key manager or Hardware Security Module (HSM) in the cloud. Key management servers are appliances (virtual or in hardware) that are responsible for the keys through their lifecycle from creation, use to destruction. HSMs are robust, resilient devices for creating and protecting cryptographic keys – an organization’s crown jewels. You may also choose to combine the use of both a KMS and HSM to benefit from both the granular management of keys underpinned by an HSM root of trust. These work in harmony with the CSP providing crypto functions/keys on demand, but increase the organization’s control, ownership, and possession.
A third approach is to use the CSP’s native key manager (Amazon Web Services KMS, Azure Key Vault etc.) with enhancements from a 3rd party vendor which facilitates increased control for the organization. Often this approach is described as Bring You Own Key (BYOK) or the preferred terminology by the Cloud Security Alliance (CSA) is Cloud Key Management System with External Origin Key. The cryptographic keys are still passed to and used by the CSP however the provenance and assurance that the key is created by the organization from a high assurance entropy source, entirely under the control of the organization means the organization has significantly improved its level of control.
Figure 1: Illustrating the shift in key ownership, control and possession across a range of deployment options
Entrust offers a range of solutions that can help organizations choose the right level of ownership, control and possession that meets their security needs in single and multi-cloud deployments. The relationship between key ownership, control and possession in a range of deployment models is illustrated in the figure above.
Entrust KeyControl is a virtual KMS appliance for managing the encryption keys via Key Management Interoperability Protocol (KMIP) for disparate virtualized workloads offering BYOK to multiple CSPs including AWS and Microsoft Azure. Entrust DataControl provides encryption agents for multi-cloud workload encryption. Of course, ownership, control and possession should always be complemented with a strong root of trust. Entrust nShield as a Service is a subscription-based model for accessing an nShield HSM platform hosted in the cloud.
The Cloud Security Alliance offers a range of key management documents that help inform organizations of the considerations, deployment options, and risks when they migrate to the cloud. The latest CSA publication – for which I played a small part as reviewer – is Recommendations for Adopting a Cloud-Native Key Management Service with External Origin Key available to download here.
You might be wondering what happened to the Ferrari California Spyder in Ferris Bueller’s Day Off? Well let’s just say it didn’t end well for the lovely car with high value ignition key. In the cloud its reassuring that organizations have a variety of options when it comes to managing keys and hopefully you won’t come across too many shady parking valets!
The next blog in this series will dig into more detail on Entrust KeyControl and its bring your own key/ manage you own key capabilities in multi-cloud deployments.